More dispatches from the front for this week’s post. Cloudflare, a premier cloud hosting and security provider was compromised back in September 2016. Several lines of faulty code in an HTML parser allowed user session data (cookies, credentials, keys, tokens, etc.) to be scattered about unrelated web sessions by the millions. This data was apparently spread in plain-text and is very difficult to remediate since the information was randomly dropped into unrelated sessions across a massive customer base. According to Cloudflare, the worst data leakage occurred between February 13 – 18th 2017.
I was approached by Snapmunk to provide commentary on this issue, which I did. However I have also have provided similar advice to clients more times than I care to count. We can point back to when the Heartbleed bug was identified back in 2014 but had been running rampant since 2012. Remediation of this issue isn’t the investment of a boatload of expensive tech solutions but can tackle this problem
Here a few of the tips I have provided:
1. What steps would you advise businesses affected by Cloudflare’s data leak take following the leak? How should they go about damage control?
They should immediately activate their breach incident response program. Then coordinate with Cloudflare on a daily basis to ensure they have the latest information on the scope and impact of the Cloudbleed breach. Depending on where the company is located they may have to contact state and local authorities that they have been impacted by the Cloudbleed.
The most proactive damage control would be to contact the users of your company’s services immediately. State what actions you are taking to address the breach and have a defined plan to follow up with those customers to keep them informed.
Internally these companies must review their security posture from top to bottom. Ensure that the CloudBleed incident did not compromise credentials that can access corporate assets and cause further security breaches in the future.
2. What can we learn from a breach like this?
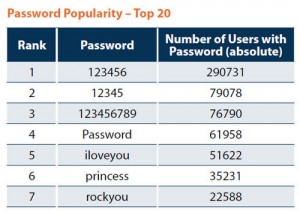
We can assume that Cloudflare was using the latest security technologies with a focus on a “Defense-in-Depth” strategy. However one error in a line of code invalidated millions of dollars in expensive technology. The takeaway for both consumers and companies is no technology service is 100% percent secure. Companies will need to aggressively review software for vulnerabilities. This will sometimes mean very expensive software migrations from legacy applications. On the consumer side, customers have to realize that using the same password for multiple sites, especially sensitive ones, is a very bad idea.