Not really.
Security risks for 2016 look a whole lot like those for 2015 and, if we are honest, 2005.
Alright, so nothing really new, but what are the biggest vulnerabilities and threats facing US businesses?
The top attack surfaces are going to be mobile devices (smartphones & tablets), cloud services, unpatched vulnerabilities and poor security risk management. Unpatched vulnerabilities has been the top target of malicious actors since the beginning of computer hacking. With the OPM breach and the details surrounding it, it provides malicious third parties the impetus to continue pushing in that direction.
Securing data in the Cloud can be problematic, before the added complexity of managing the data on a mobile device. However, mobile platforms (phones, tablets, etc.) are becoming the access point of choice for the enterprise and so this issue needs to be addressed swiftly.
What should a companies’ leadership do to prepare for or thwart a cyber security attack and data breach?
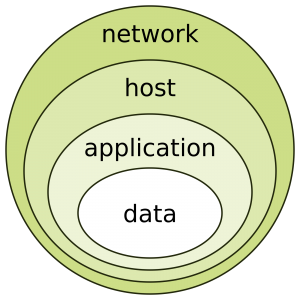
Defense-In-Depth. That should be a phrase that all enterprise leadership should understand.
Security attacks and breaches cannot be wholly stopped or prevented, no matter what type of technological and personnel controls are implemented. If a malicious actor wants to break into a person’s or companies’ sensitive information, they will find a way. It may not be a technical approach, it could be using very reliable social engineering techniques.
Security breaches based on technical vulnerabilities are growing in scope and visibility due to the increasing automation and interconnectedness of systems, mobile devices and the sharing of personal data. The financial incentive is there for the criminal, nation-state, malicious actors to perpetrate these crimes.
Cyber-security preparedness in the business community, while becoming more visible in recent years, is still far behind the curve when compared to those who wish to commit cybercrime. There is still a tremendous disconnect with employees and general public regarding the current security threats and what impacts their behavior have in propagating or thwarting a breach.
Whatever solution the enterprise implements for data security it should follow the security principles of Confidentiality, Integrity and Availability. Data confidentiality entails the protection of sensitive information from unauthorized users. Data integrity encompasses changes to the data and the identification of the individual or system that changed it. Availability is whether or not the data can be accessed by users or systems when required.
There are some basic components to an effective security program that do not involve large technology expenditures. One is to keep your infrastructure (servers, workstations, networking gear) up to date (software patches, hardware refreshes), physical security around critical components, endpoint protection (anti-virus / anti-malware) and user training. Most security breaches gain a toe-hold due an error by the user or malicious user intent. For example, the Target breach was propagated by phishing emails.
One of the most effective security practices that employees can participate in is to be cautious when responding to email and browsing the Web. Employees need to make sure that they understand the risks when opening email attachments or clicking on links from unfamiliar sources, for these can lead to malware or virus infection. This is best covered in an effective security education program.
Sensitive data contained within emails is bounced around multiple servers where copies of this data be stored. Utilizing an encrypted email client is a cost effective way of reducing the risk of a data breach via email.
There are additional security technical controls that can be implemented to protect data in the cloud. Mobile Device or Mobile Application Management (MDM/MAM) software installed on a user’s mobile device is a good first step in securing and controlling sensitive corporate data in the cloud via a mobile platform.
Unencrypted emails, chat and photos is a large risk when stored on a mobile device. When the device is lost, which happens often, then this information could be extracted. Having the right controls (technical and risk management) for your enterprise mobile device infrastructure is key.
On the risk management process side, organizations should know what is riding on their network and accessing their applications. With appropriate asset, network, log and mobile device management controls this would be a relatively “easy” process. However certain industries, healthcare and government for example, lacks a certain IT maturity level that other industries take for granted (see Financial). Establishing proper asset management and data management processes and procedures should be a high priority for industries with sensitive information.
All of these basic tips contribute to a “Defense-in-Depth approach or layered to enterprise security.
I’d be interested to hear your opinion in the comments below!
Leave a Reply